Xiaomi’s preinstalled Security App, known as ‘Guard Provider’ Had a Backdoor
According to Security services provider, CheckPoint, Xiaomi was carrying threat to privacy and security in their pre-installed apps. This application is the Guard Provider (com.miui.guardprovider), a security app developed by Xiaomi that includes three different antivirus programs packed inside it, allowing users to choose between Avast, AVL, and Tencent.
Basically, Guard Provider sends and receives network traffic in an unsecured nature, and itself becomes a security threat, allowing a threat actor to connect to the same Wi-Fi network as the victim and carry out a Man-in-the-Middle (MiTM) attack. Then, as part of a third-party SDK update, the attacker could disable malware protections and inject any rogue code he chooses such as to steal data, implant ransomware or tracking or install any other kind of malware.
CheckPoint promptly disclosed this vulnerability to Xiaomi, and the phone manufacturer released a patch shortly after.
The analysis itself provides us with a valuable insight in to the attack scenario. The first stages are below and for the rest you can visit CheckPoint.
Before explaining the potential attack scenario, it is important to point out that there are actually some hidden disadvantages in using several SDKs within the same app. Because they all share the app context and permissions, these main disadvantages are that:
- A problem in one SDK would compromise the protection of all the others.
- The private storage data of one SDK cannot be isolated and can therefore be accessed by another SDK.
With the case of Xiaomi Guard Provider, we show below how a Remote Code Execution (RCE) attack is possible when integrating two SDKs with problematic behavior.
Briefly put, due to Guard Provider’s network traffic from any Xiaomi device being unsecured, this allows it to be intercepted via a Man-in-the-Middle (MiTM) attack and inject rogue code as part of a third-party SDK update. Let’s look at the possible attack scenario.
Stage 1: Catch the Avast Update
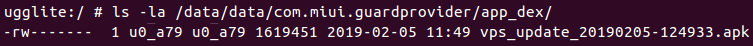
By default, with Avast set as the app’s security scanner, the app periodically updates its virus database by downloading the avast-android-vps-v4-release.apk APK file to Guard Provider’s private directory: /data/data/com.miui.guardprovider/app_dex/vps_update_<timestamp>.apk.
This APK file is then loaded and executed by Avast SDK before the scan of the device and contains the timestamp when the file was downloaded. For example, vps_update_20190205-124933.apk.
Fig 2: Avast update file.
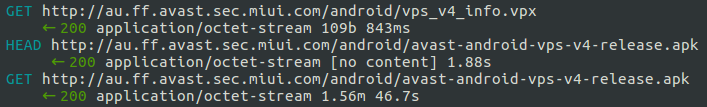
Unfortunately, due to the fact that the update mechanism uses an unsecured HTTP connection to download this file, a threat actor, via a MiTM attack, can detect the timing of the Avast update and predict what the disk’s APK file name will be next. The attacker needs simply to intercept the response part of the http://au.ff.avast.sec.miui.com/android/avast-android-vps-v4-release.apk connection.
Figure 3: Avast update traffic
Hold this thought in mind, as the predicted file name of the Avast update will then be used in the second step of the attack.
By way of the initial interception, the MITM attacker is thus able to prevent future Avast updates by responding with a “404 error” to http://au.ff.avast.sec.miui.com/android/vps_v4_info.vpx requests.

0 comments:
Post a Comment